PANOS SSH Issue, No Matching Host Key Type Found. Their Offer ssh-rsa
After upgrading PANOS on my firewall from 10.1 from 10.2, I was no longer able to SSH into the firewall. Trying to SSH into management interface resulted in the following SSH error:
❯ ssh [email protected]
Unable to negotiate with 192.168.1.1 port 22: no matching host key type found. Their offer: ssh-rsa
The issue is related to weak host key algorithms from the firewall and updated SSH clients (I’m not sure why this has changed from 10.1 to 10.2!) However, SSH clients now treat ssh-rsa as deprecated and deemed insecure. You can allow insecure ssh-rsa from your SSH client by using the following flag to SSH (better solution later in this article, as the following is less secure):
❯ ssh -oHostKeyAlgorithms=+ssh-rsa [email protected]
To confirm exactly what the firewall is providing we can use nmap and a ssh test script:
❯ nmap --script ssh2-enum-algos 192.168.1.1
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-10 12:11 GMT
Nmap scan report for 192.168.1.1 (192.168.1.1)
Host is up (0.011s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
| ssh2-enum-algos:
| kex_algorithms: (9)
| curve25519-sha256
| [email protected]
| ecdh-sha2-nistp256
| ecdh-sha2-nistp384
| ecdh-sha2-nistp521
| diffie-hellman-group-exchange-sha256
| diffie-hellman-group16-sha512
| diffie-hellman-group14-sha256
| diffie-hellman-group14-sha1
| server_host_key_algorithms: (1)
| ssh-rsa
| encryption_algorithms: (6)
| [email protected]
| aes128-ctr
| aes192-ctr
| aes256-ctr
| [email protected]
| [email protected]
| mac_algorithms: (10)
| [email protected]
| [email protected]
| [email protected]
| [email protected]
| [email protected]
| [email protected]
| [email protected]
| hmac-sha2-256
| hmac-sha2-512
| hmac-sha1
| compression_algorithms: (2)
| none
|_ [email protected]
161/tcp closed snmp
443/tcp open https
The problematic part is:
| server_host_key_algorithms: (1)
| ssh-rsa
While we have a working solution, it is better to configure the firewall not to provide the deprecated and insecure ssh-rsa. To do this configure a SSH service profile:
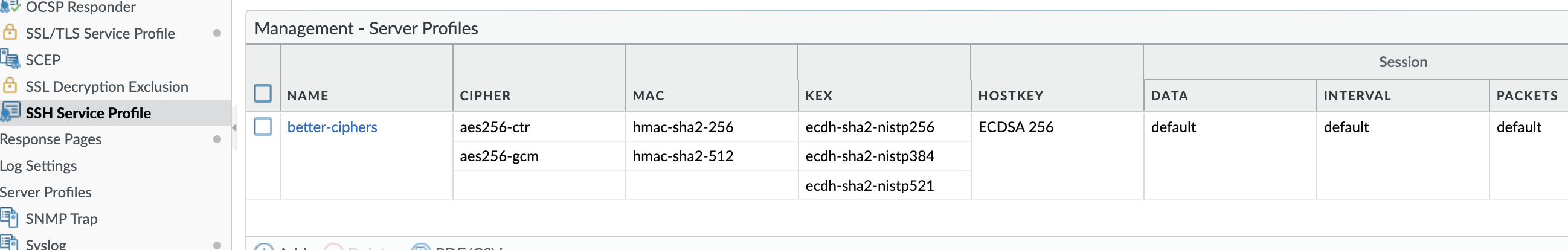
Then apply that to the management interface:
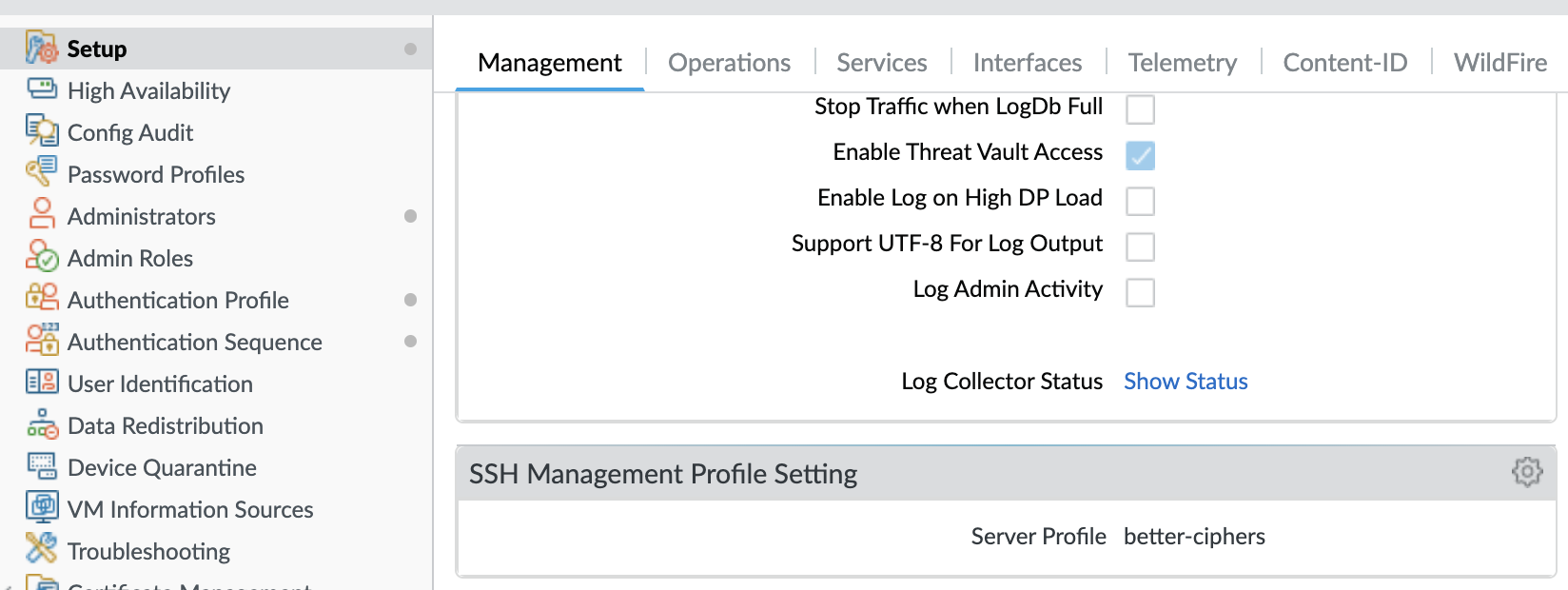
Rather than use the web interface you can use the following commands on the cli. First enters config mode and then create a SSH service management profile called “better-ciphers”, then adds minimal ssh profile options. It then sets the system to use the new SSH service management profile. It will then commit, once completed the next line restarts the ssh service from configure mode which is required for the settings to take effect (lines marked with # are just comments for clarity):
# enable configure mode
configure
# create profile
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers
# create ciphers in new profile
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers ciphers aes256-ctr
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers ciphers aes256-gcm
# create hostkey in new profile
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers default-hostkey key-type ECDSA 256
# create session key exchange algorithms in new profile
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers kex ecdh-sha2-nistp256
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers kex ecdh-sha2-nistp384
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers kex ecdh-sha2-nistp521
# create message authentication codes in new profile
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers mac hmac-sha2-256
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers mac hmac-sha2-512
# create settings for auto rekeying of session keys in new profile
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers session-rekey data default
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers session-rekey interval default
set deviceconfig system ssh profiles mgmt-profiles server-profiles better-ciphers session-rekey packets default
# switch system to use new SSH profile for management interface
set deviceconfig system ssh mgmt server-profile better-ciphers
# commit 😀
commit
# run restart ssh demon from configure mode
set ssh service-restart mgmt
# drop out of configure mode
exit
Once completed we can test again with nmap:
❯ nmap --script ssh2-enum-algos ed.thewayeye.net
Starting Nmap 7.94 ( https://nmap.org ) at 2024-01-10 12:22 GMT
Nmap scan report for ed.thewayeye.net (192.168.1.1)
Host is up (0.013s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
| ssh2-enum-algos:
| kex_algorithms: (3)
| ecdh-sha2-nistp256
| ecdh-sha2-nistp384
| ecdh-sha2-nistp521
| server_host_key_algorithms: (1)
| ecdsa-sha2-nistp256
| encryption_algorithms: (2)
| aes256-ctr
| [email protected]
| mac_algorithms: (2)
| hmac-sha2-256
| hmac-sha2-512
| compression_algorithms: (2)
| none
|_ [email protected]
443/tcp open https
Nmap done: 1 IP address (1 host up) scanned in 45.59 second
As we can see the troublesome ssh-rsa has now been removed and at the same time we have removed weaker ciphers etc, so this is preferable. Referenced mostly from Palo here. Test this first before touching anything close to production, as you can lose SSH access. This was tested without ssh keys so I’m not sure if the impact on those. Again refer to the Palo documentation quoted above. As long as you have web access to the management you should be able to revert when testing.