Sniffing Network Traffic in ESX
If you want to enable promiscuous network sniffing within a vSwitch the safest way to do it is to create a second port group. Promiscuous mode can be enabled on an existing port group but once this has been done, any device connected to that port group has that ability.
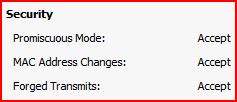
Once you have your second port group correctly configured you can attach a monitoring appliance. To do my monitoring I tend to use OpenBSD with tcpdump and then use Wireshark to analyse the data. Log into your OpenBSD machine and bring up the NIC without allocating it an IP:
Ifconfig vic0 up
Once that is up you can start capturing data:
tcpdump -i vic0 -s 1500
When you have your data you can import it into Wireshark to filter out the uninteresting traffic. It seems that if you do not include a VLAN tag in your promiscuous mode port group you can capture the network traffic from your trunked VLAN port. You can use Wireshark to filter the VLAN you are interested in from your packet capture output: