Listing Live DNS Requests
Sometimes you want to see exactly what a computer or application is trying to communicate with. Obviously you can take full a network packet capture and filter the results and correlate the behavior with the DNS traffic, but sometimes it is easier to watch these results live as they happen. One quick way to do this is use Wireshark, however not the full client but the command line version tshark. Tshark allows you to filter on specific facets of DNS giving you a cleaner output especially when you are only interested in domains that an application is talking to. To get a list of domains we will be filtering DNS queries and responses. Before we start we need to work out which interface to capture on. list the current interfaces from the OS from a command prompt or terminal using:
tshark -D
This will return a list of your current network interfaces/capture options. On my machine I got the following:
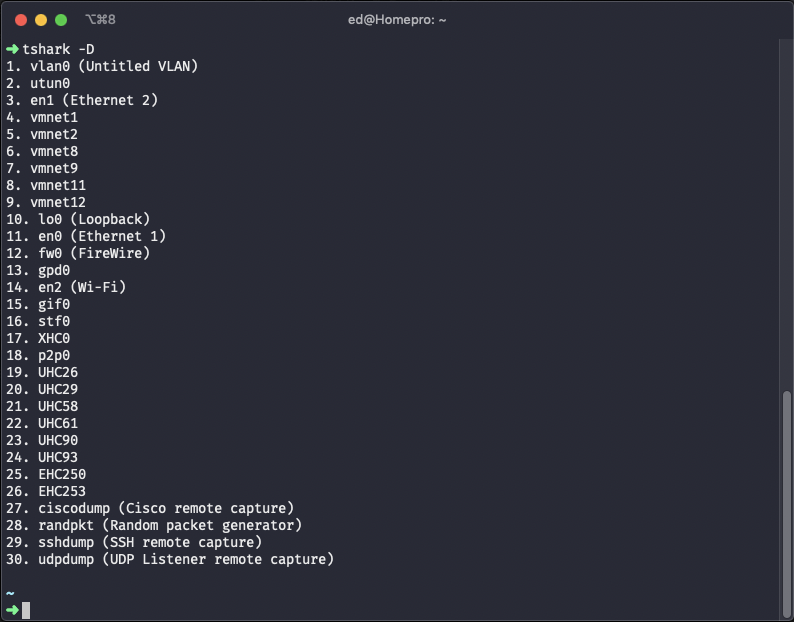
It is worth noting that you are not limited to physical interfaces. Other interesting options are virtual interfaces or remote interfaces. The same method described here is equally effective at monitoring DNS traffic for virtual machines or even VPN tun interfaces like GlobalProtect or Cisco AnyConnect. The above output has a selection of vmnet* (VMware Fusion) interfaces and gpd0 (Palo Alto GlobalProtect) The interface I’m using in this example is my main wired interface en1. Make a note from the above output the number of the interface. In this case it is 3 which you need to pass with the -i flag. To start the capture use the following:
tshark -i 3 -T fields -e ip.src -e dns.qry.name -Y "dns.flags.response eq 0"
Running this for 23s and doing a google ping gave the following output:
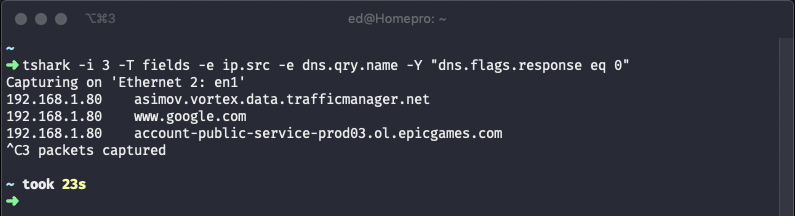
A bit boring but we can see the expected domain list including google domain, also we can see some activity from some other background applications. If you leave it running you get a feel for how much DNS is used and how important it is. Looking into the rest of the command we are printing with -e the source IP and query name fields while the filter -Y is including only the DNS query rather than include the response. If you are more interested in including the response then use:
tshark -i 3 -T fields -e ip.src -e dns.qry.name -Y "dns.flags.response eq 1"
If you want to perhaps exclude NXDOMAIN noise from the responses then use:
tshark -i 3 -T fields -e ip.src -e dns.qry.name -Y "dns.flags.response eq 1 && ! dns.flags.rcode eq 3"
You can be quite creative with the filters.
The original idea for this came from here quite a long time ago. Some of the syntax in that original command has been depreciated.
For further information about the Wireshark DNS filter go here